In the previous post; The human factor in cybersecurity: Employees, we have seen how human factor affects the overall cybersecurity posture of an organization. We classified employees as unwitting and malicious and saw how unwitting employees get duped in compromising the organization’s security policies. We also learned about a methodology to educate the unwitting employees and empower them to be more responsible and accountable. In this post, we are going to deal with malicious employees.
Typical threats a business faces from malicious employees are:
- Misuse of company resources
An example of this may be using a company-provided computer to access and store illegitimate content.
- Data theft
An example of this may be theft of the company’s intellectual property.
Cybersecurity analysts attribute various reasons for employees to turn malicious and most of these could be categorized in one of the cells in the below honeycomb.
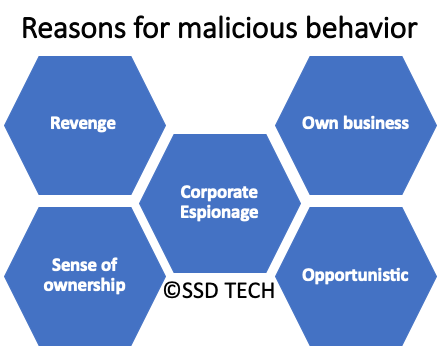
Let us look at these with some examples:
Revenge: Employees get disgruntled when they perceive they have been treated unfairly by their managers or by their co-workers. This emotion can lead them to commit crimes against their company just to teach a lesson to their tormentor. Typically we have seen this behavior when an employee has been terminated from service, their reactions could range from deleting all business data from their work PCs to in extreme cases, planting malware in their employer’s infrastructure that may cause greater havoc and loss for the employer.
Own business: There may be some employees who have entrepreneurial aspirations, these employees snoop around their employer’s business to learn its secrets like customer or supplier information that could help them set up a competing business.
Sense of ownership: In our experience, we have come across some employees who are highly possessive about the data that is under their care and this may impede data sharing for the overall good of the business. Examples of these are sales personnel not updating the CRM or the ERP resulting in management getting skewed sales reports. This may look very insignificant but has a domino effect on the overall business strategy.
Opportunistic: Typically these are second-streamers who are out to abuse the company resources for personal gains. An example could be employees illegally earning money by offering the company’s toll-free phone access to non-related parties for a fee.
Corporate espionage: Usually when we discuss insider threat, the first thought that races through one’s mind is corporate espionage. While this threat is not uncommon, it has gained unnecessary hype. A typical SMB seldom faces this threat, unless they are associated with a vital or critical business sector like defense or research. Businesses in vital or critical sectors are typically a magnet for saboteurs who spy on the business for competitors or enemy states to gain access to all secrets that may be of value to their actual bosses.
The business assets that risk damage by malicious employees are:

Sensitive or confidential data that are governed by legal mandates
This can be customer data such as personal health information or personally identifiable information that is regulated by legal frameworks. Any compromise of this type of customer data could have severe legal and financial implications on the business.

Business secrets
These are typically trade secrets of the company like intellectual property or ongoing research work.
Now having identified the factors that induce employees to be malicious and the business assets that are at high risk, we will now look at the ways to protect your business from insider threat. The below table shows the list of controls that are available to address insider threats:
| Control Type | Description | Example |
| Preventive | Controls designed to prevent incidents from occurring. | Access controls to applications and systems that prevent unauthorized individuals from performing transactions |
| Detective | Controls designed to alert the management when incidents occur. | Reports that show suspicious activities. |
| Corrective | Controls that lessen the impact on the organization when incidents occur | Business continuity plan |
| Administrative | Controls that align with the board-approved risk appetite and inform employees of management’s expectations. | Policies or procedures that guide the implementation of the information security program. |
| Technical | Software and /or hardware that prevents unauthorized activities | Application firewall that prevents logical access to an application |
| Physical | Controls to prevent unauthorized physical access to the assets. | Locks and keys |
With so many different controls given above it may be an undaunting task to select the controls that will specifically address the requirements of the business. It is therefore advisable to take professional advice and assistance in choosing or designing the control(s) that can address the risks faced by the business.
About the author
Sudhakar S Narayan is a Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), and Certified lead auditor in ISO Information Security Management System (ISMS) and ISO Business Continuity Management System (BCMS). He has more than two decades of experience in Information Assurance. He is currently a Principal Consultant and Director at SSD Tech.



